Finding vulnerable devices on your network is easy. Simply navigate to the topology or inventory and search for "Vulnerable" or "vulnerable". A list of all vulnerable hosts will appear and the topology will gray out all hosts that do not match your search criteria.
Left-click on the desired host within the search results to find it within the topology. Then click on the host to populate the Inspector with more information about the host, to include the CVEs identified.
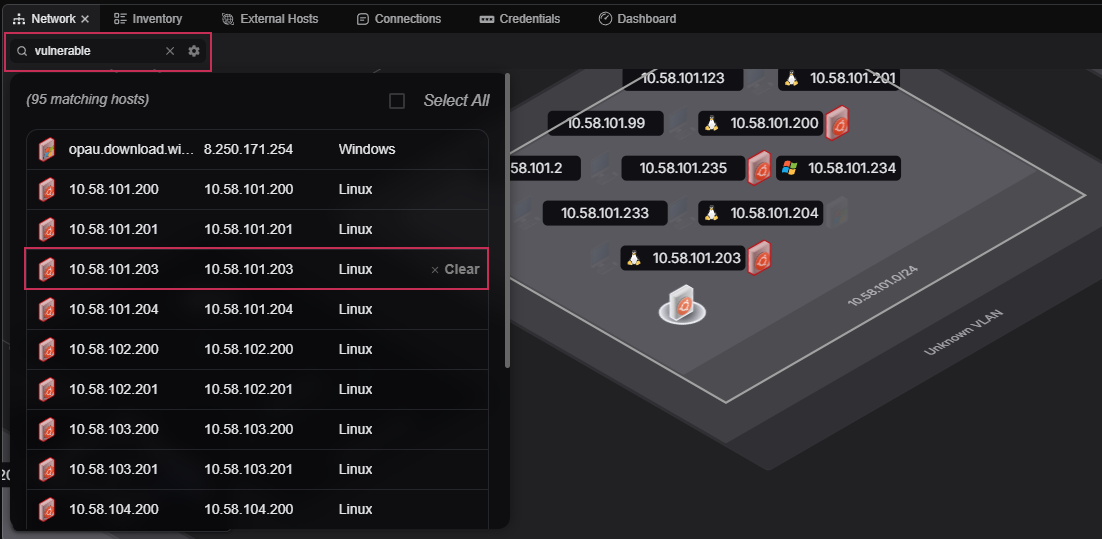
Additionally, users can search within the Inventory tab to find vulnerable devices. All hosts containing the Vulnerable tag will be displayed. Any host which does not contain the tag will be temporarily hidden.
